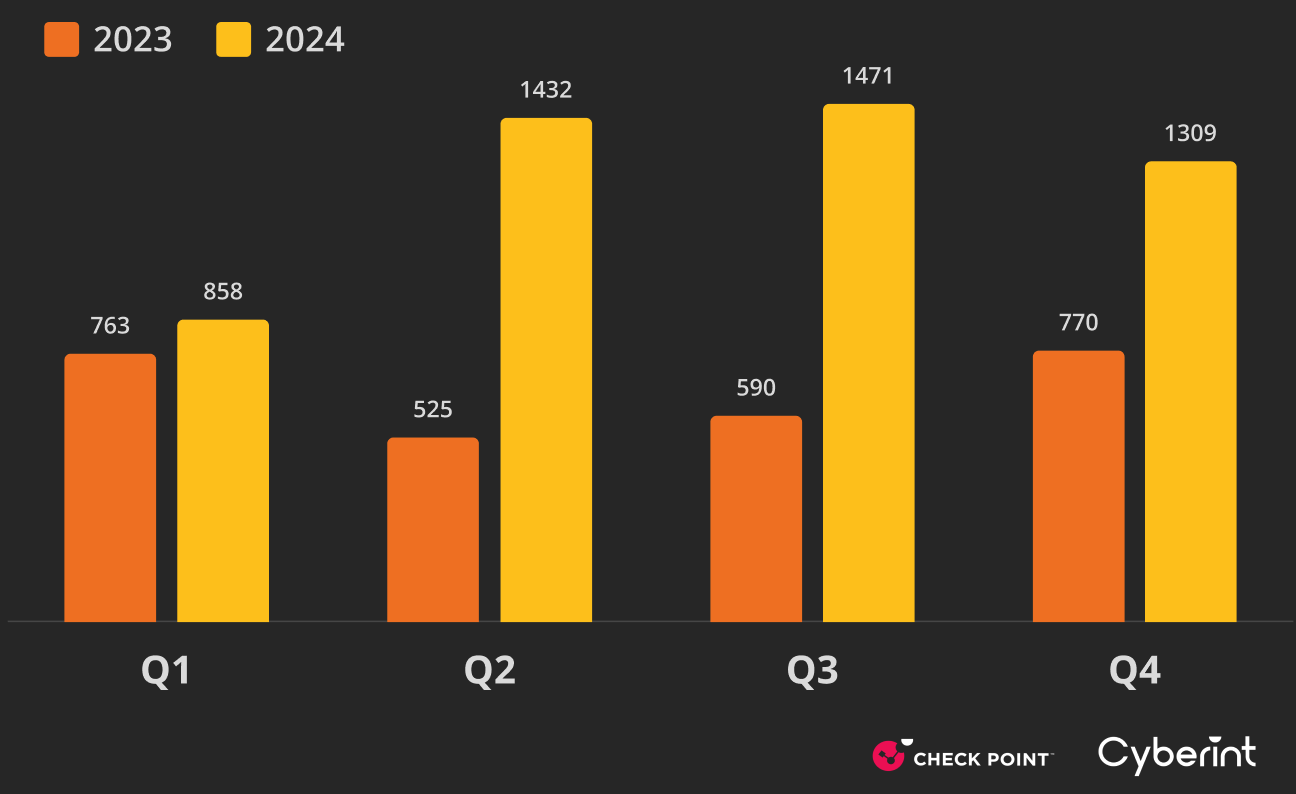
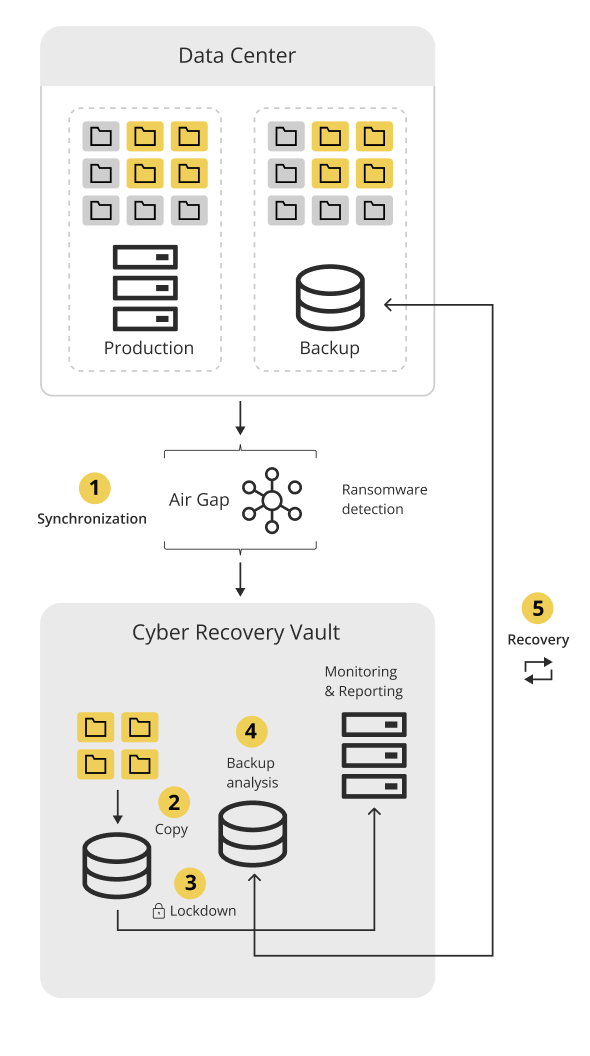
2025 marks a pivotal moment in the fight against ransomware. In the first quarter alone, attacks surged by 126% compared to the same period last year - this is the highest increase in history. According to Check Point Research, the pace of threats is accelerating at an unprecedented rate, and the scale of the problem is no longer an isolated incident.
ENISA estimates that over 650 companies fall victim to ransomware every month - 200 more than the previous year. Attacks are becoming more sophisticated, faster, and more effective.
The success of these attacks is driven by the professionalization of the cybercriminal market. For criminals, this means easier access to ready-made tools and a lower barrier to entry. For companies, it translates to higher risks and tougher defenses.